Table of Contents
Highlights
- Herodotus mimics human typing rhythms to evade timing- and behavior-based detection used by banks and mobile security.
- Delivered via smishing and Accessibility abuse, it intercepts SMS OTPs and uses overlays to steal credentials.
- The Trojan, after installation, can intercept incoming SMS messages, reveal one-time passwords, display overlay pages to steal passwords, and take control of apps remotely to carry out fraudulent bank transfers.
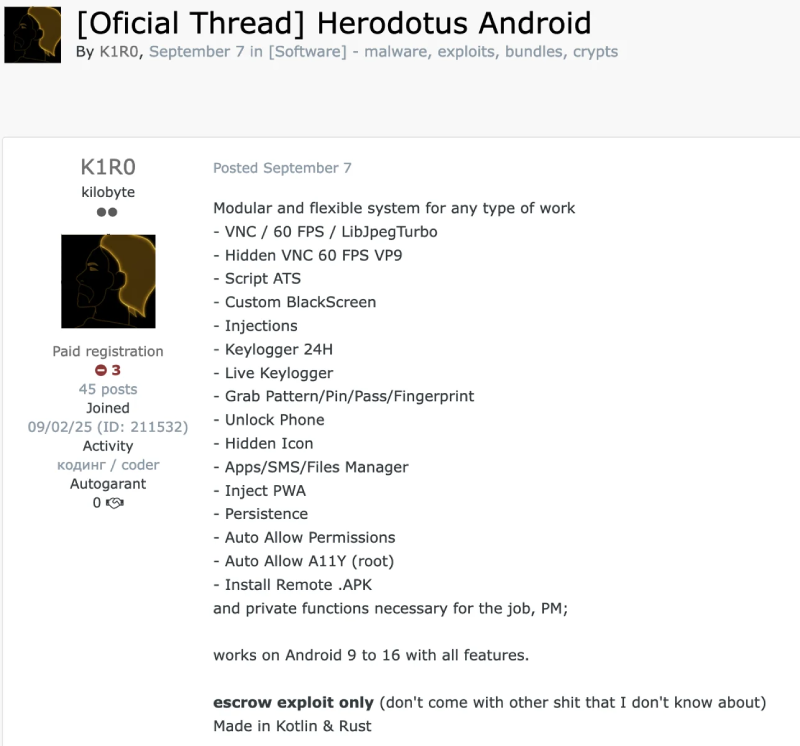
A new Android banking trojan named Herodotus has emerged that deliberately mimics human interaction patterns to slip past behavior-based detection systems. Security researchers at ThreatFabric and multiple reporting outlets describe Herodotus as a malware-as-a-service platform.
The operators of this malware are already deploying it in targeted smishing campaigns against users in Italy and Brazil. The malware is notable not just for classic mobile fraud techniques but for introducing timing and input randomness intended to defeat rhythm- and timing-based anti-fraud checks.
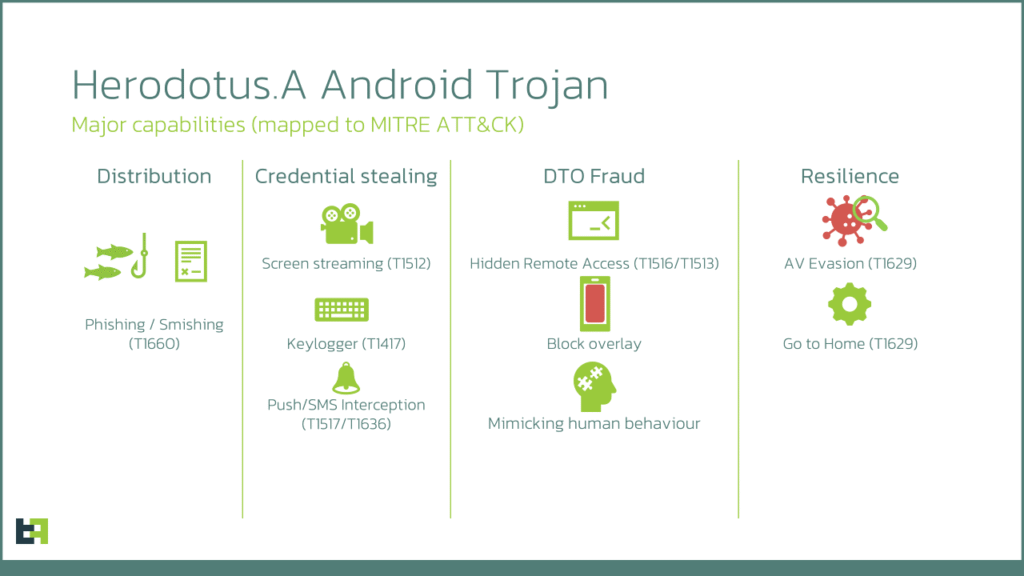
How Herodotus Works
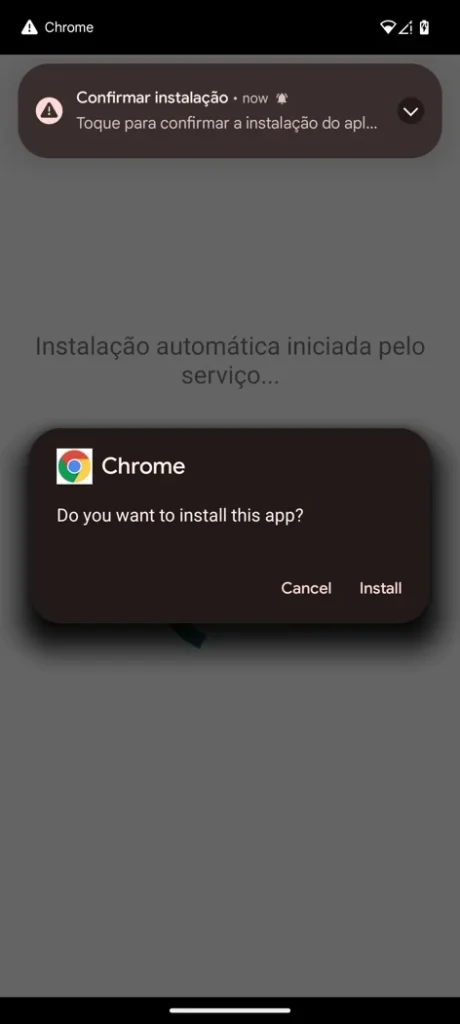
Herodotus combines several well-known device takeover (DTO) tactics with a novel focus on human-like input simulation. Attackers deliver the initial payload through SMS phishing links that install a custom dropper. That dropper exploits the Accessibility service workflow to obtain elevated control, using overlay screens to hide the permission-granting steps while the user thinks a benign loading screen is displayed. Once installed, the trojan can intercept SMS messages to capture one-time passwords, deploy overlay pages to harvest credentials, and remotely control apps to initiate fraudulent bank transfers.
What differentiates Herodotus from many predecessors is its random delay injection within input routines. Rather than sending rapid, predictable automated keystrokes, the malware injects variable pauses and typing patterns that mimic human hesitations and rhythms. This undermines detection rules and anti-fraud heuristics that assume bots type uniformly fast or follow mechanical timing patterns.
Why Human Mimicry Matters
Anti-fraud and behavioral biometrics systems often flag anomalous input characteristics, such as consistent inter-keystroke intervals, unnaturally fast navigation, or repetitive timing patterns. By introducing stochastic delays and more organic input traces, Herodotus reduces the signal that these systems rely on to classify sessions as automated or fraudulent.
In practice, this means that a remote attacker controlling a compromised phone may appear to be the legitimate human owner, typing and navigating the device, making transactions and authentication flows appear legitimate to both banks and device-monitoring tools.
Beyond defeating timing checks, the malware’s combined use of SMS interception and overlay attacks means attackers can both obtain 2FA codes and show victims convincing fake interfaces to capture credentials. The Accessibility abuse ensures broad control, even on recent Android versions, including devices running Android 13 and later, by guiding users through permission acceptance and then completing sensitive actions in the background.
Who Is Being Targeted
Current campaigns attributed to Herodotus focus on Italy and Brazil, regions where observers have seen active smishing distribution and successful device-takeover incidents. Threat actors are marketing Herodotus through a MaaS model, enabling a spread of financially motivated groups that may not themselves possess deep development skills. The MaaS structure speeds adoption and iteration, increasing the urgency for financial institutions and mobile security vendors to adapt detection strategies.
Defensive Measures and Recommendations
Defending against Herodotus requires a layered approach that moves beyond simple timing heuristics. Security teams should consider combining these measures:
- Hardened permission flows: Make Accessibility and overlay permission requests more transparent to users and limit automatic enabling pathways.
- Multi-factor anomaly signals: Correlate device environment signals such as app visibility changes, unexpected accessibility service activation, and SMS interception attempts with behavioral scores rather than relying solely on keystroke timing.
- App hardening and verification: Encourage banking apps to implement strong app integrity checks and to detect overlay attempts or background activity inconsistent with the foreground session.
- User education on smishing: Reinforce recognition of suspicious SMS links and the risks of granting accessibility permissions to unknown apps.
- Endpoint monitoring: Deploy mobile threat detection that flags suspicious Accessibility API use and overlays, and that inspects for process injection or dropper behavior.
Outlook
Herodotus illustrates a concerning trend: adversaries are increasingly engineering malware to imitate legitimate human behavior rather than just automating attacks. That shift complicates detection but also creates an opportunity for defenders to evolve.
By fusing behavioral biometrics with richer contextual telemetry and stronger permission controls, institutions can restore discriminatory power even against malware that deliberately “acts human.” The rapid spread of Herodotus’s MaaS underscores the need for coordinated defensive updates across vendors and banks, as well as user awareness campaigns, to limit the Trojan’s impact.