Table of Contents
Highlights
- TVM Software uncovers hidden risks in third-party vendors before they become security threats.
- Protects your business reputation by preventing data breaches caused by unvetted vendor systems.
- Ensures continuous compliance with real-time monitoring, not just one-time certifications.
A celebrity chef decided to cook for strangers and give the common folk an experience of his coveted Michelin Star restaurant. He selected downtown NY as the perfect place and set up a cart for a four-course meal with disposable cutlery on the curbside. He did not want people to be offended by freebies, so he priced the food but nominally.
It’s New York, and everyone loves to try something new, so within a few hours of opening, there was a mad rush, and his food was sold out. But considering his best trait does not leave his side, he asked for public feedback; then came the stark revelation, people loved his food and felt he could price it more, and they were willing to pay if it wasn’t for the bad quality cutlery that had.
So, this celebrity chef learns the hard way that even the most exquisite food can be ruined by flimsy disposable spoons. The meal? Perfect. The experience? Undermined by something as seemingly insignificant as cutlery. Now, here’s the kicker: this isn’t just about food. Swap out the spoons for unchecked third-party vendors in the business world, and suddenly, you’ve got a full-blown crisis simmering on the back burner.
Businesses today are like master chefs crafting five-star digital experiences, but if their third-party vendors, those supplying everything from cloud storage to payment gateways, aren’t vetted for threat and vulnerability management software, well, let’s just say the whole operation is one weak spoon away from disaster. You wouldn’t trust a rickety food cart to serve gourmet meals, so why do companies blindly trust vendors with their most sensitive data?
The Unseen Threats Lurking In Your Supply Chain
Let’s talk about the invisible cracks in the foundation, the ones most businesses don’t see until it’s too late. That Michelin-star chef thought his only job was to cook, but the real failure wasn’t in the recipe; it was in the overlooked details. The same goes for companies that lean on third-party vendors without asking the hard questions.
Here’s the thing: TVM Software isn’t just a fancy buzzword; it’s the difference between a secure operation and a ticking time bomb. Yet, scores of businesses treat vendor security like an afterthought, assuming someone else has done the homework. Newsflash: they probably haven’t.
Take the recent surge in supply chain attacks. Hackers aren’t always brute-forcing their way in; they’re slipping in through the side door, the one left unlocked by a vendor who didn’t patch their software or skimped on encryption. And when that happens, it’s not just the vendor who pays the price. The fallout lands squarely on the business that trusted them.

Think of it like this: you wouldn’t hire a contractor to build your house without checking if they use subpar materials. So why would you let a vendor handle your data without ensuring they’ve got airtight security? The answer’s simple: convenience. But in the digital world, convenience without caution is a recipe for disaster.
The fix? Audit relentlessly. Demand transparency. And for heaven’s sake, make sure every vendor in your chain has their Threat and Vulnerability Management Software on lock. Because in the end, your reputation isn’t just about what you serve, it’s about how well you ensure nothing spoils the dish.
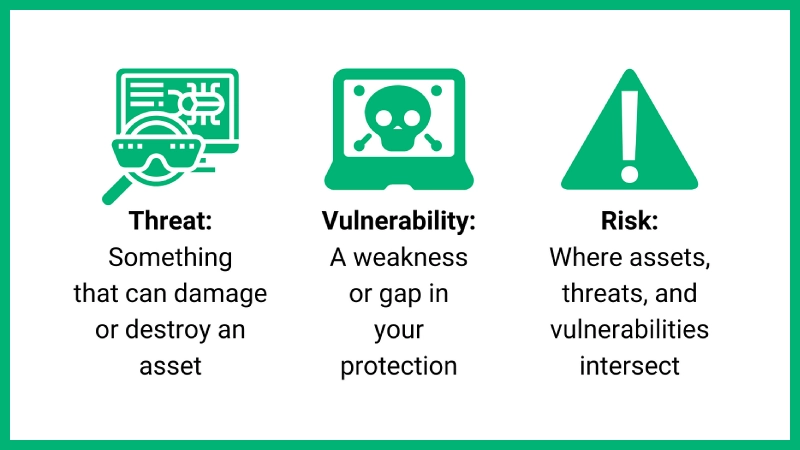
Threats You Can’t See: How TVM Software Detects The Invisible Risks Lurking In Your Vendor Ecosystem
The Silent Backdoor Problem
You wouldn’t hand a stranger the keys to your house and assume they’ll remember to lock up—so why do it with your data? Third-party vendors often have deep access to your systems, and if their security is lax, hackers don’t even need to break in. They can just stroll through the digital backdoor. Threat and Vulnerability Management (TVM) Software acts like a no-nonsense security guard, scanning vendor networks for unpatched flaws, weak passwords, and suspicious activity before they become your problem. The best way to avoid a breach is to make sure the door is never left open in the first place.

The “Oops, We Forgot To Update” Syndrome
Imagine a restaurant still using the same rusty can opener from 1998—gross, right? Yet, businesses work with vendors running outdated, unsupported software all the time. Hackers love this. Known vulnerabilities in old systems are like flashing neon signs saying, “Attack here!” TVM tools don’t just spot these aging weak points; they force the issue, flagging vendors who treat updates like optional homework. Because in cybersecurity, “we’ll get to it later” usually means “we’ll get hacked tomorrow.”
The Shadow IT Surprise
Ever order a salad and get a side of something… unexpected? That’s what happens when vendors use unauthorized tools (Shadow IT) without telling you. Maybe it’s a random cloud storage app or an unapproved messaging platform—either way, it’s a security blind spot. TVM Software shines a light on these rogue systems, sniffing out hidden risks before they turn into full-blown disasters. After all, you can’t protect what you don’t know exists.
The Compliance Mirage
Some vendors treat security audits like a pop quiz they can cram for the night before. They’ll pass the compliance check, but their actual security? Flimsier than a disposable spoon. TVM tools go beyond surface-level certifications, continuously monitoring for real-time threats instead of just rubber-stamping paperwork. Because in cybersecurity, what’s on paper matters—but what’s happening behind the scenes matters more.

Summing It Up
The world runs on partnerships, sure. But when those partners skip crucial security checks, they become backdoors for cybercriminals. And it’s not some whimsical, far-off threat; it’s happening right now. A single unpatched vulnerability in a vendor’s system can unravel years of trust, leaving customers (and reputations) in the digital dumpster.
So, what’s the takeaway? If you’re going to serve up excellence, you better make sure every piece of the puzzle, down to the last disposable spoon, can hold its own. Because in business, as in cooking, the little things make or break the experience.